Solution Tabs
The ASM solution experience is organized into three tabs that guide you from design to execution to outcomes:Builder Tab
Design and customize the ASM workflow. This view shows the prebuilt ASM workflow graph and lets you tailor modules (for example, Seeding, Discovery, Enrichment) and parameters to your environment, add open‑source or in‑house tools, and define inputs and outputs. The Builder is where you configure the exact workflow used for ASM.Modules used in the ASM Workflow
- Enumerate Hostnames via OSINT Sources: Passive subdomain discovery from curated OSINT sources; no API keys required, with optional keys to expand coverage.
- Enumerate Hostnames via Root Domain DNS Brute Force: Brute forces subdomains on root domains using trusted resolvers and wildcard filtering; supports custom wordlists.
- Enumerate Hostnames via DNS Permutations Brute Force: Finds environment/region variants by permuting known hostnames; includes built-in and custom wordlists.
- Enumerate Hostnames via Recursive DNS Brute Force: Expands to deeper DNS levels focusing on high-probability candidates; supports level‑2/3/4 wordlists.
- Generate Custom DNS Wordlists: Builds targeted wordlists from discovered hostnames for both root and recursive brute force.
- Enumerate DNS Records: Resolves DNS records for hosts and extracts resolving hostnames, IPs, and related assets.
- Scan for Open Ports: Scans common ports across hosts and outputs detailed per‑port findings and convenient host:port lists.
- Fingerprint Network Services: Identifies services and gathers metadata (protocols, banners, products) from open ports.
- Probe for Web Servers: Detects HTTP/HTTPS services and collects titles, redirects, TLS data, and more; also surfaces related hostnames.
- Fingerprint Web Technologies: Detects web technologies like servers, CMS, CDNs, and WAFs with contextual metadata.
- Enumerate Hostnames via Crawling: Crawls discovered web servers to extract additional hostnames from HTML, headers, and scripts.
Configure and Execute ASM
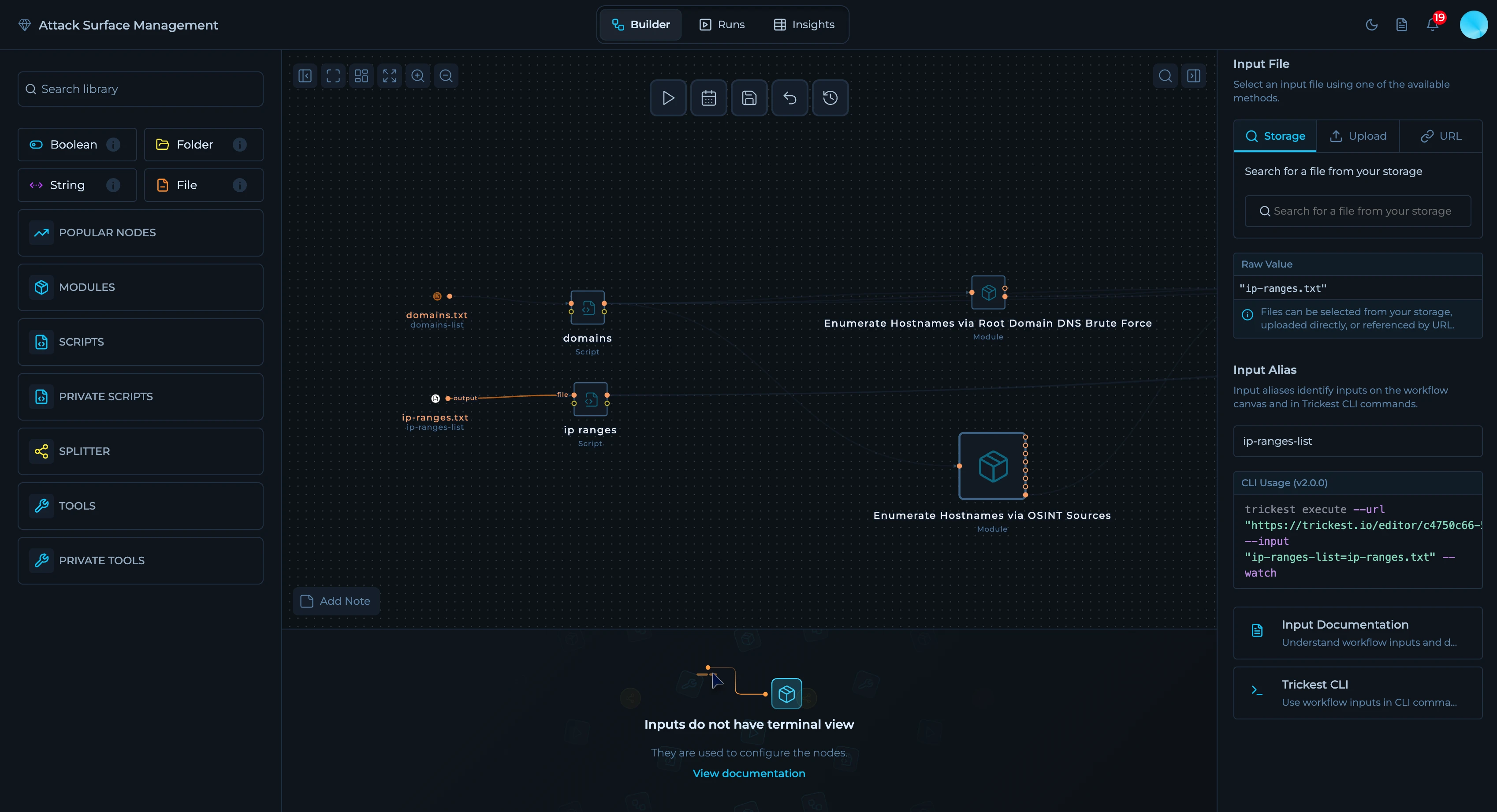
File Inputs
- Domains (domains.txt): Root domains to seed discovery (for example,
example.com,corp.example.com). - IP ranges (ip-ranges.txt): Include targets beyond DNS (for example,
203.0.113.0/24).
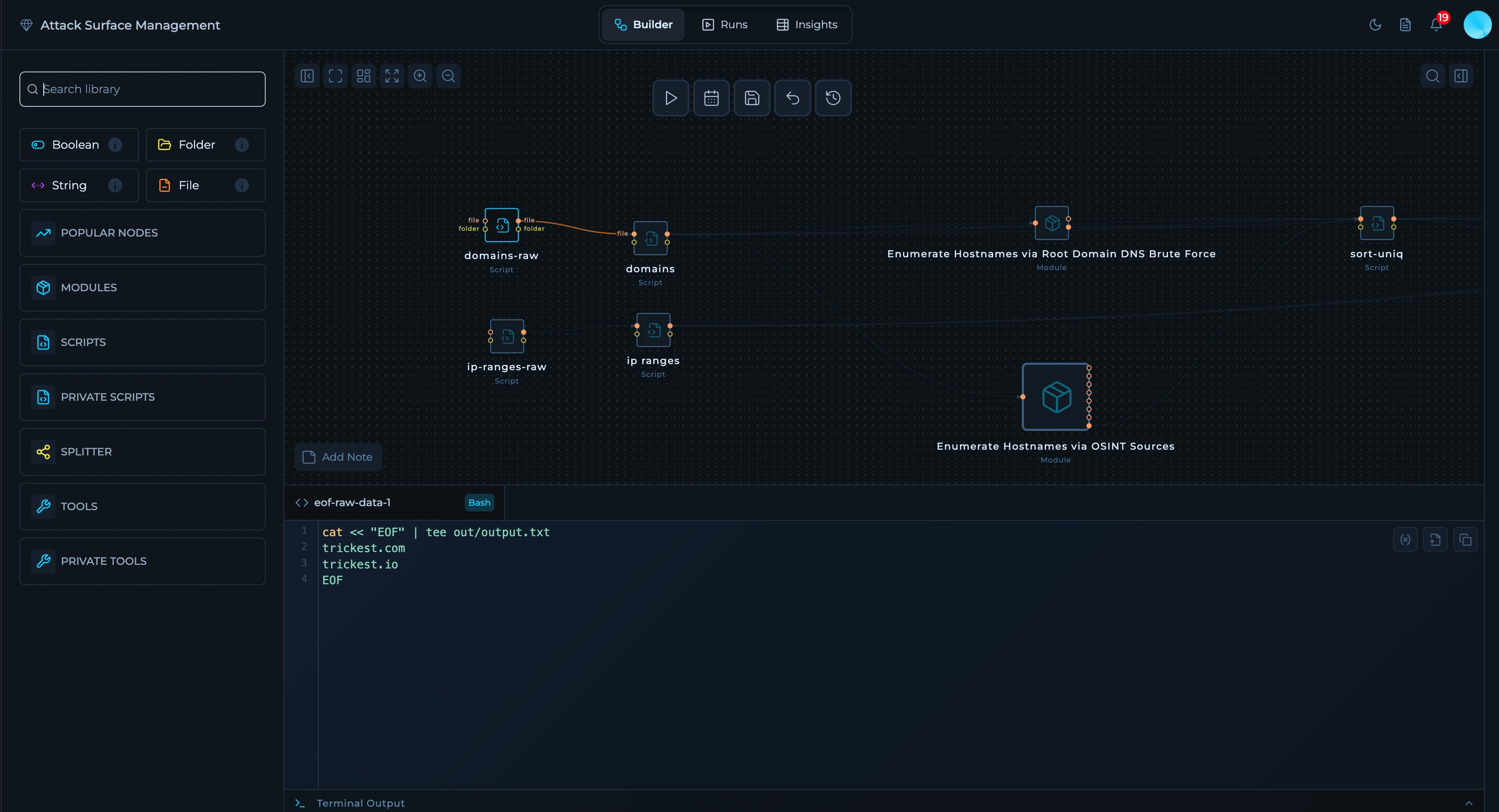
Provide Inputs via Script
Steps- Add a script node and output your list (one per line) to
out/output.txt. - Connect its output to discovery modules (domains) and to resolution/enrichment stages (IP ranges).
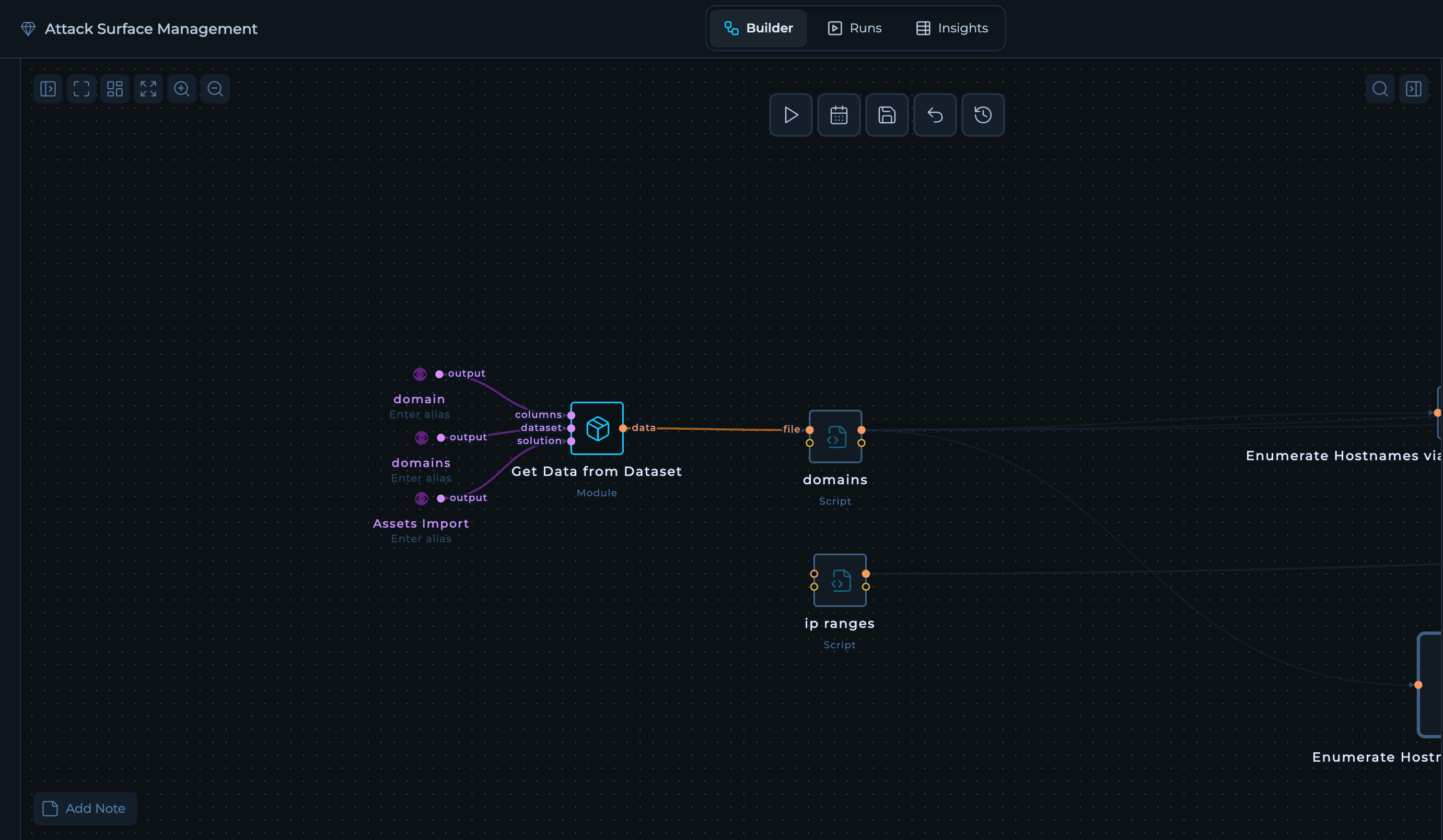
Provide Inputs via Modules or Integrations
Use the Get Data from Dataset module to pull your domains and IP ranges from an existing dataset and feed them straight into the ASM workflow. Think of it as “selecting” the right column from your source of truth and sending it forward — no manual files needed.If you already maintain a solution dataset with assets, this is the easiest way to keep ASM in sync. When the dataset updates, your next run picks up the changes automatically.
- Drag the
Get Data from Datasetmodule into the canvas. - Point it to your asset dataset (for example, “Assets Imported”).
- Use one instance to output domains, and another to output IP ranges.
- Connect each module’s
dataoutput to the matching ASM inputs
- Domains: one domain per line (for example,
example.com). - IP ranges: one entry per line (for example,
203.0.113.0/24or198.51.100.10).
Integrations: With custom modules, this step can connect to any system you use — CMDBs, asset inventories, data warehouses (S3, BigQuery), spreadsheets, ticketing, or threat intel — as long as the module outputs a simple newline‑delimited list.
Run Tab
A specific execution of the workflow in time. You can start on‑demand or scheduled runs, monitor node‑level progress and logs, and review artifacts produced by each node. On the left sidebar you can see each node output and the status of the node. On the right sidebar you can see run list and when solution was executed.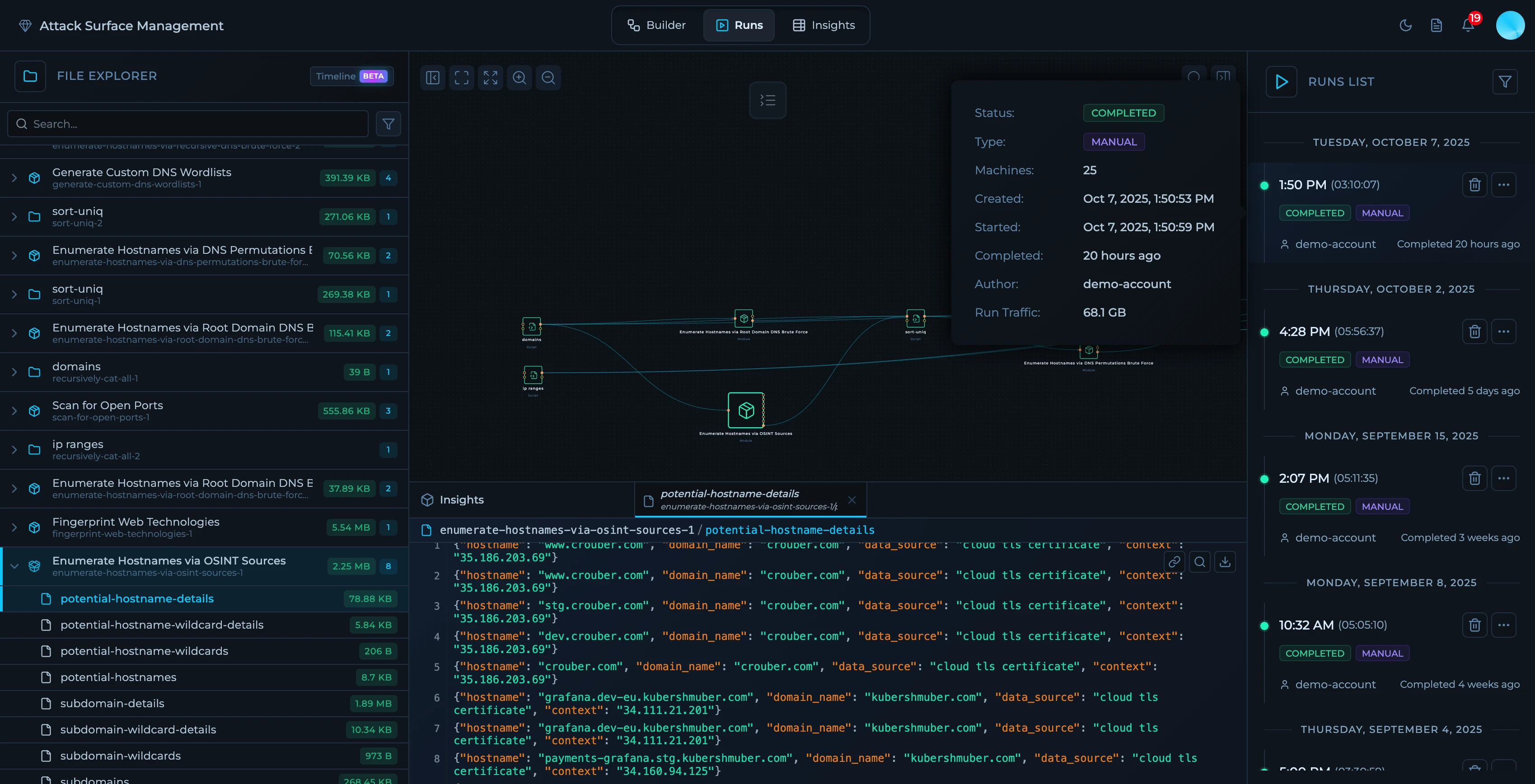
For more information about workflow execution, check Monitoring Runs.
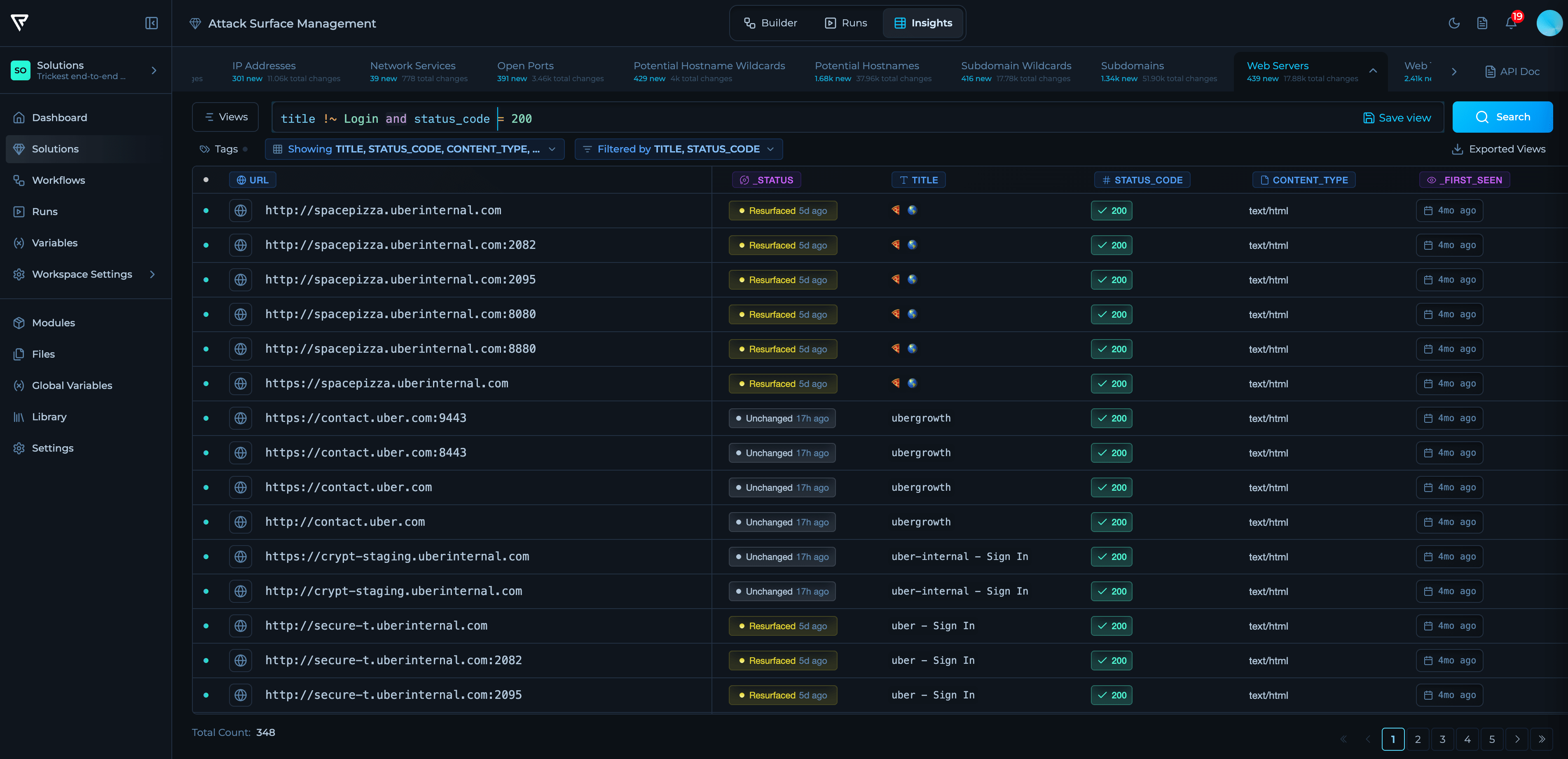
Insights
Explore the results generated by the workflow. View consolidated assets, changes over time (new, removed, resurfaced), technology fingerprints, open ports and services, and web exposure. Insights provides deltas, trends, and context to help prioritize follow‑up actions and integrate with downstream systems.
For more information about insights, check Insights.
Looking to adapt this Solution to your environment? See Custom Solutions for patterns and best practices.
Solution API
You can access Solutions API programmatically to list solutions, browse datasets, and fetch results. Most users don’t need to memorize endpoints—when you open any Solution in Trickest, you’ll find an “API Docs” panel with ready‑to‑use snippets (curl, Python, JavaScript) tailored to your workspace and the selected dataset.Where to find it: Open a Solution → Click on 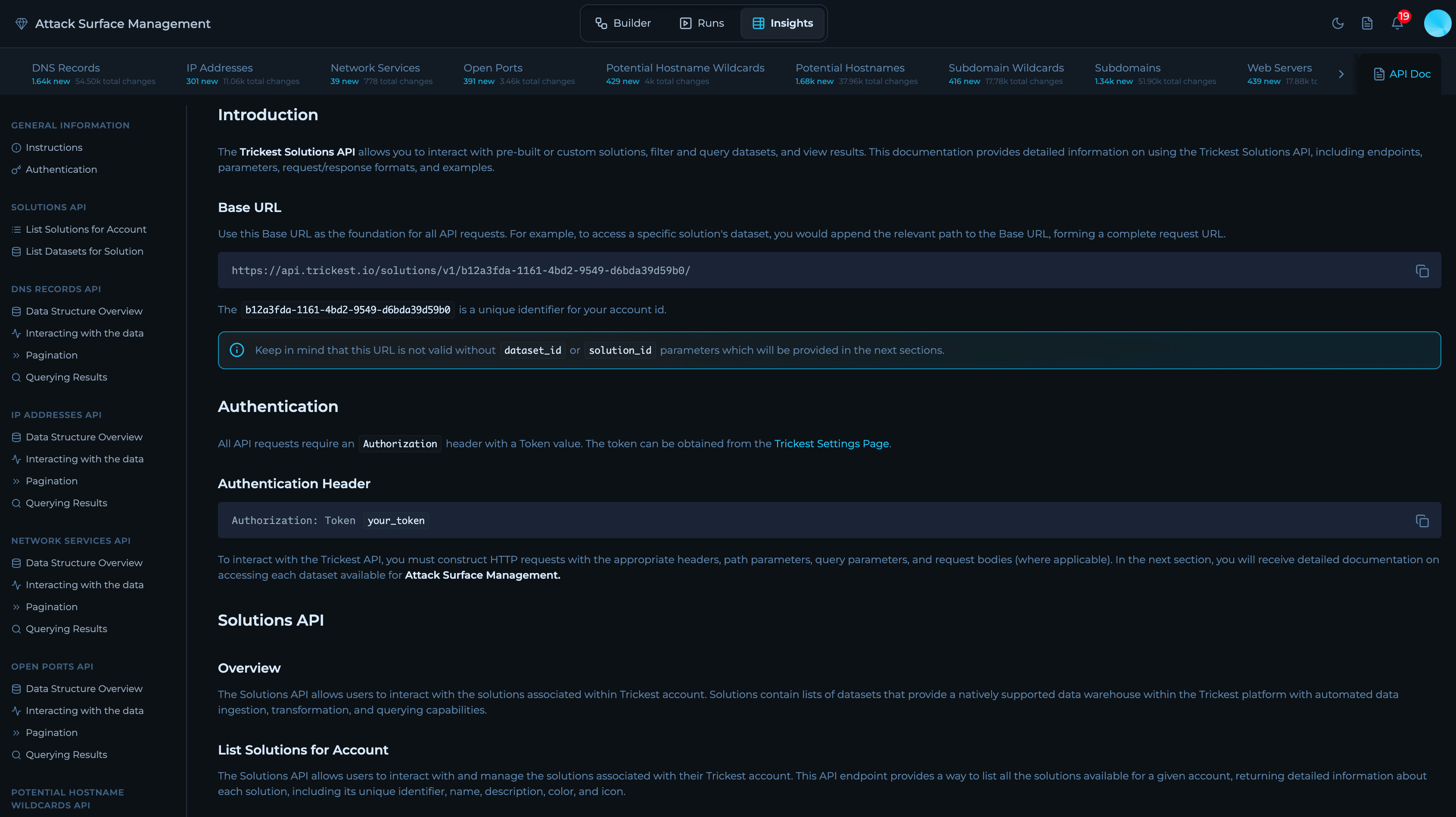
API Docs button. It shows the correct base URL, your vault‑scoped endpoints, and example requests you can copy and run.