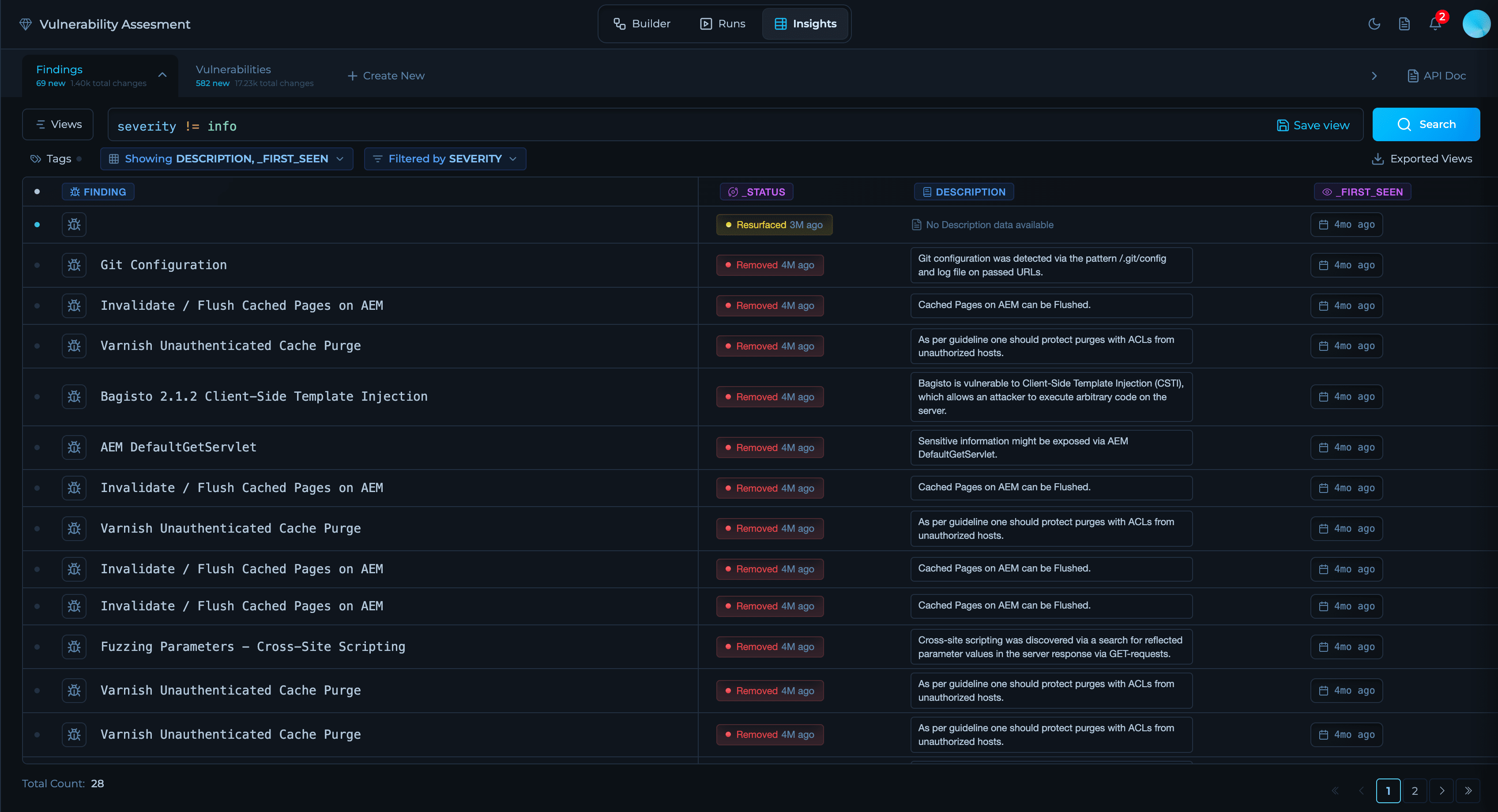
Solution Tabs
The Vulnerability Assessment solution experience is organized into three tabs that guide you from design to execution to outcomes:Builder Tab
Design and customize the Vulnerability Assessment workflow. This view shows the prebuilt workflow graph and lets you tailor modules for scanning, enumeration, vulnerability detection, and reporting to your environment. Add open-source or in-house tools, define inputs and outputs, and configure the exact workflow used for vulnerability assessment.Modules used in the Vulnerability Assessment Workflow
Data Integration
- Get Data from Dataset: Pulls new assets from Attack Surface Management datasets (Web Servers, Open Ports, Network Services) for continuous vulnerability assessment.
Web Application Vulnerability Scanning
- Scan for Outdated Software: Identifies outdated software versions with known vulnerabilities (CVEs).
- Scan for Exposed Admin Panels: Detects publicly accessible administrative interfaces and control panels.
- Scan for Misconfigured Software: Identifies common misconfigurations in web servers, frameworks, and applications.
- Scan for Sensitive Files: Discovers exposed sensitive files like configuration files, source code, and internal documentation.
- Scan for Exposed Backups: Detects publicly accessible backup files (SQL dumps, archives, configuration backups).
- Scan for Exposed Secrets: Identifies exposed credentials, API keys, tokens, and other sensitive information.
Network Service Vulnerability Scanning
- Scan Network Services for Weak Credentials: Tests network services (SSH, FTP, databases) for weak or default credentials.
- Scan Network Services for Misconfigurations: Detects misconfigurations in network services that could lead to security vulnerabilities.
The workflow operates as a continuous security layer on top of Attack Surface Management, automatically scanning newly discovered assets for vulnerabilities without requiring manual asset enumeration.
Configure and Execute Vulnerability Assessment
The Vulnerability Assessment solution is designed to continuously scan new assets discovered by Attack Surface Management for vulnerabilities. The workflow automatically queries ASM datasets for newly discovered assets and feeds them into vulnerability scanning modules.How It Works
1
Pull web server URLs from ASM
Gets the
url column from the Web Servers dataset where _status = new. These URLs feed into web application scanners that check for outdated software, exposed admin panels, misconfigurations, sensitive files, backups, and secrets.2
Pull open port data from ASM
Gets
ip_address, port, and hostname from the Open Ports dataset where _status = new. This data feeds into network misconfiguration scanners.3
Pull network service details from ASM
Gets
ip_address, port, hostname, and protocol from the Network Services dataset where _status = new. This data feeds into weak credential scanners for SSH, FTP, and databases.Default Configuration
By default, the workflow is configured to scan assets from the Attack Surface Management solution: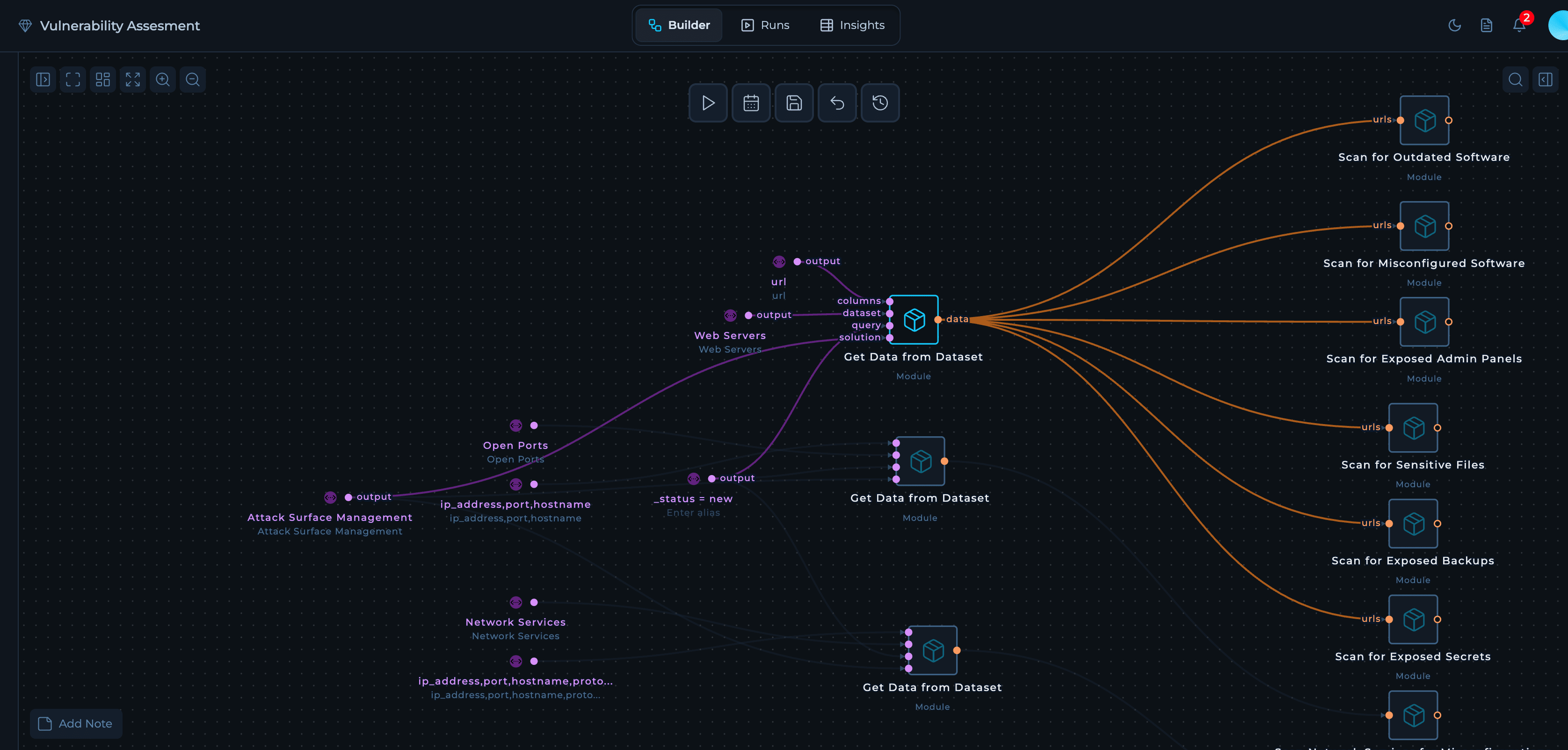
Customizing Data Sources
You can modify the dataset queries to scan different asset sets: Scan all assets (not just new ones)Solution input to pull from other solutions (e.g., DAST, custom solutions) or use different datasets within ASM.
For query syntax and available operators, see Query Language Syntax.
Alternative Input Methods
If you’re not using Attack Surface Management, you can provide inputs directly: File Inputs Replace the dataset modules with file inputs containing your targets:Run Tab
A specific execution of the workflow in time. You can start on-demand or scheduled runs, monitor node-level progress and logs, and review artifacts produced by each node. On the left sidebar you can see each node output and the status of the node. On the right sidebar you can see run list and when solution was executed.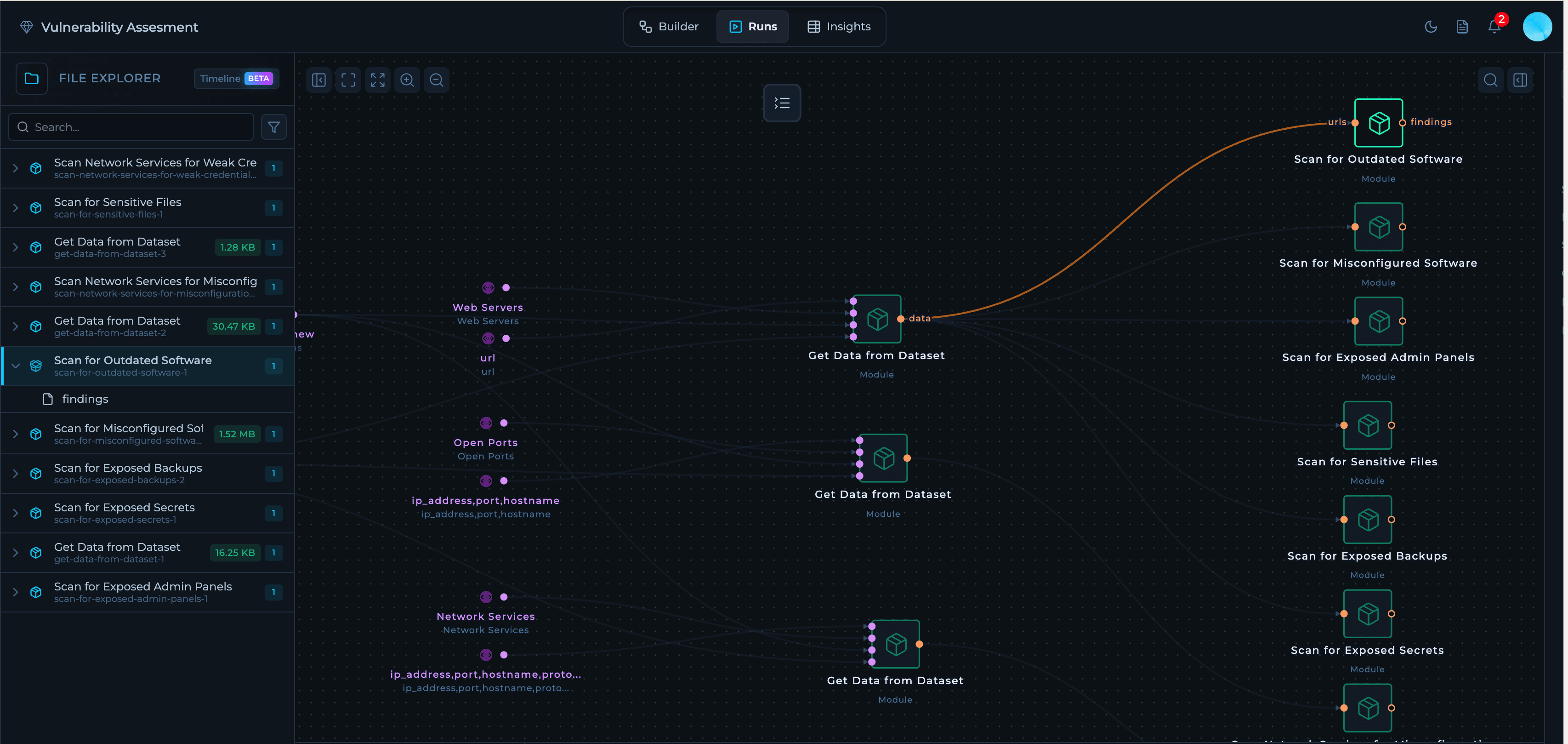
For more information about workflow execution, check Monitoring Runs.
Insights
Explore the results generated by the workflow. View consolidated vulnerabilities, changes over time (new, fixed, resurfaced), severity distribution, affected assets, and compliance posture. Insights provides deltas, trends, and context to help prioritize remediation actions and integrate with downstream systems.
For more information about insights, check Insights.
Looking to adapt this Solution to your environment? See Custom Solutions for patterns and best practices.
Solution API
You can access Solutions API programmatically to list solutions, browse datasets, and fetch results. Most users don’t need to memorize endpoints—when you open any Solution in Trickest, you’ll find an “API Docs” panel with ready-to-use snippets (curl, Python, JavaScript) tailored to your workspace and the selected dataset.Where to find it: Open a Solution → Click on 
API Docs button. It shows the correct base URL, your vault-scoped endpoints, and example requests you can copy and run.