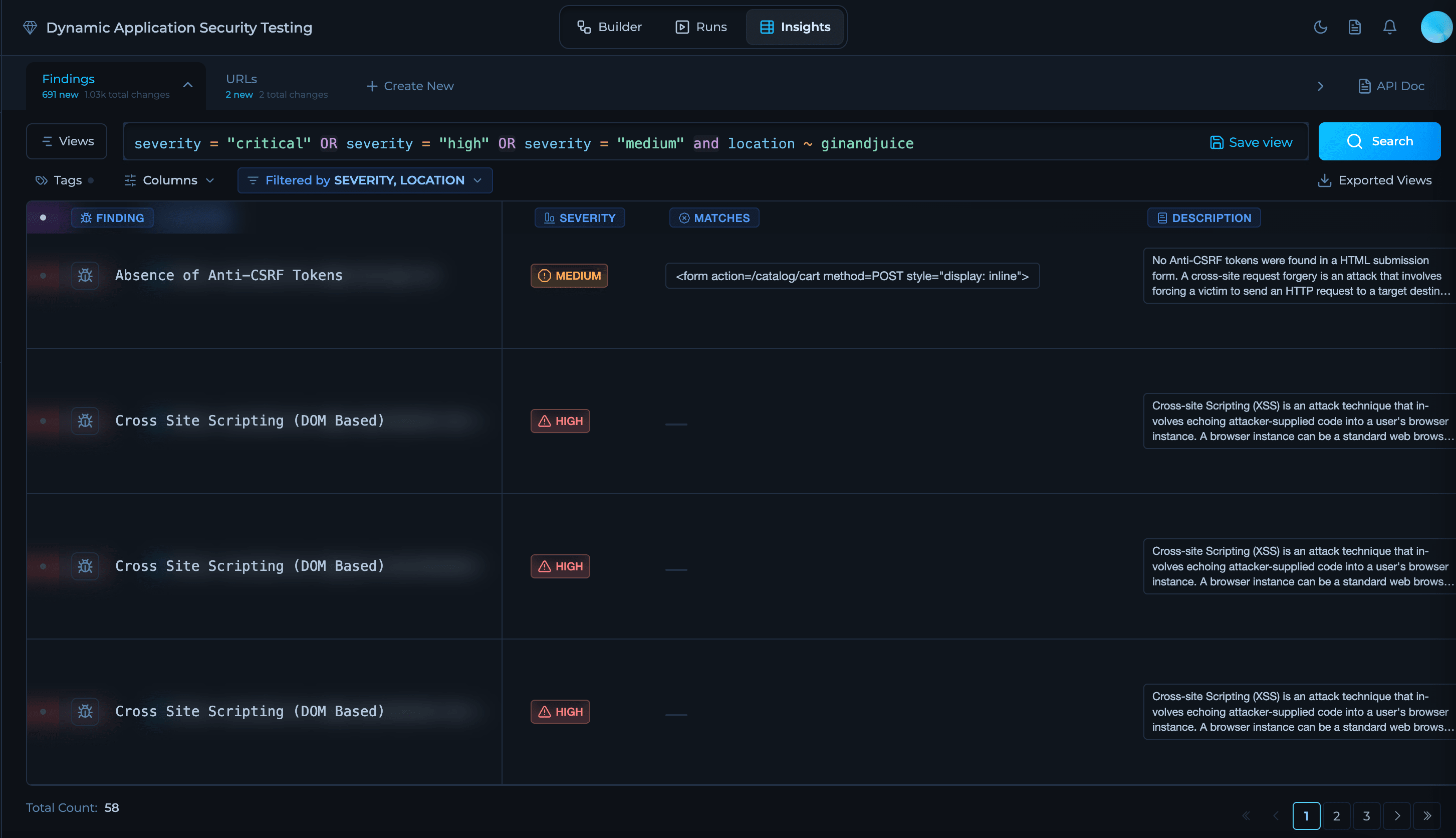
Solution Tabs
The DAST solution experience is organized into three tabs that guide you from design to execution to outcomes:Builder Tab
Design and customize the DAST workflow. This view shows the prebuilt DAST workflow graph and lets you tailor modules for discovery, scanning, analysis, and reporting to your environment. Add open-source or in-house tools, define inputs and outputs, and configure the exact workflow used for DAST.Modules used in the DAST Workflow
Discovery & Enumeration
- Probe for Web Servers: Detects HTTP/HTTPS services and collects titles, redirects, TLS data, and response metadata; surfaces related hostnames.
- Enumerate DNS Records: Resolves DNS records for hosts and extracts resolving hostnames, IPs, and related assets.
- Discover Paths via OSINT Sources: Discovers URLs and paths from public OSINT sources like Wayback Machine, Common Crawl, and URL repositories.
- Discover Paths via Crawling: Crawls web applications to extract URLs, paths, and endpoints from HTML, headers, and JavaScript.
- Discover Paths via Directory Brute Force: Discovers hidden directories and files through intelligent brute-forcing with custom and built-in wordlists.
Scanning & Fingerprinting
- Scan for Open Ports: Scans common ports across hosts and outputs detailed per-port findings and convenient host:port lists.
- Fingerprint Network Services: Identifies services and gathers metadata (protocols, banners, products) from open ports.
- Fingerprint Web Technologies: Detects web technologies like servers, CMS, CDNs, and WAFs with contextual metadata.
Content & Code Analysis
- Analyze JavaScript Code: Deep analysis of JavaScript files to extract endpoints, API calls, secrets, and generate custom wordlists for further testing.
Vulnerability Scanning
- Scan for Exposed Backups: Detects publicly accessible backup files (SQL dumps, archives, configuration backups) that may contain sensitive data.
- Scan for Exposed Secrets: Identifies exposed credentials, API keys, tokens, and other sensitive information in web responses.
- Scan for Sensitive Files: Discovers exposed sensitive files like configuration files, source code, and internal documentation.
- Scan for Outdated Software: Identifies outdated software versions with known vulnerabilities (CVEs).
- Scan for Exposed Admin Panels: Detects publicly accessible administrative interfaces and control panels.
- Scan for Misconfigured Software: Identifies common misconfigurations in web servers, frameworks, and applications.
- Scan Network Services for Weak Credentials: Tests network services (SSH, FTP, databases) for weak or default credentials.
- Scan Network Services for Misconfigurations: Detects misconfigurations in network services that could lead to security vulnerabilities.
- Scan for Technology-Specific Vulnerabilities: Identifies vulnerabilities specific to detected technologies, frameworks, and CMS platforms.
- Fuzz Web Applications for Vulnerabilities: Advanced fuzzing to detect injection vulnerabilities (SQL, XSS, SSRF, etc.) across discovered endpoints and parameters.
Reporting
- Generate Scan Report: Compiles all findings, discovered assets, screenshots, and metadata into a comprehensive HTML report.
The workflow also uses internal utility steps (such as deduplication, normalization, and correlation) to merge and enrich results between stages.
Configure and Execute DAST
The DAST solution requires four key inputs to define the scan scope and behavior:Input Parameters
Target The target hostname or URL to scan.- Single application URL (e.g.,
https://app.example.com) - Hostname (e.g.,
app.example.com)
Use custom headers to identify scan traffic, authenticate to applications, or bypass WAF detection. Each header should be on a new line.
Use out-of-scope patterns to prevent the scanner from triggering logout actions, destructive operations, or accessing sensitive administrative functions.
Configuration Examples
Basic Web Application ScanFor complex authentication flows, use the Get Cookies via Puppeteer Recording module to capture session cookies automatically. Record your login flow using Chrome’s built-in recorder, and the module will generate the Cookie header for you.
Run Tab
A specific execution of the workflow in time. You can start on-demand or scheduled runs, monitor node-level progress and logs, and review artifacts produced by each node. On the left sidebar you can see each node output and the status of the node. On the right sidebar you can see run list and when solution was executed.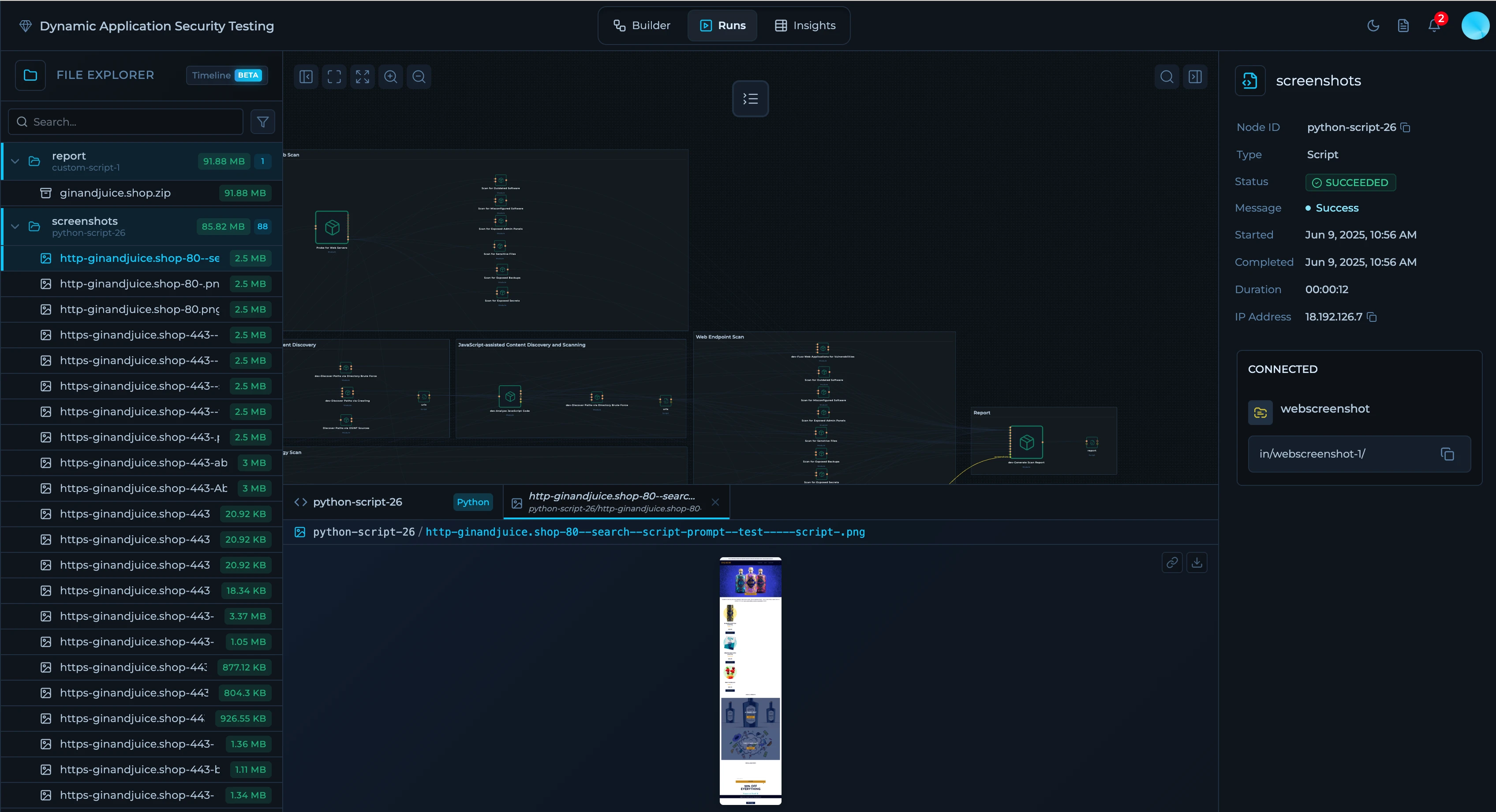
For more information about workflow execution, check Monitoring Runs.
Insights
Explore the results generated by the workflow. View consolidated vulnerabilities, changes over time (new, missing, removed, resurfaced), technology fingerprints, exposed endpoints, and security issues. Insights provides deltas, trends, and context to help prioritize remediation actions and integrate with downstream systems.
For more information about insights, check Insights.
Looking to adapt this Solution to your environment? See Custom Solutions for patterns and best practices.
Solution API
You can access Solutions API programmatically to list solutions, browse datasets, and fetch results. Most users don’t need to memorize endpoints—when you open any Solution in Trickest, you’ll find an “API Docs” panel with ready-to-use snippets (curl, Python, JavaScript) tailored to your workspace and the selected dataset.Where to find it: Open a Solution → Click on 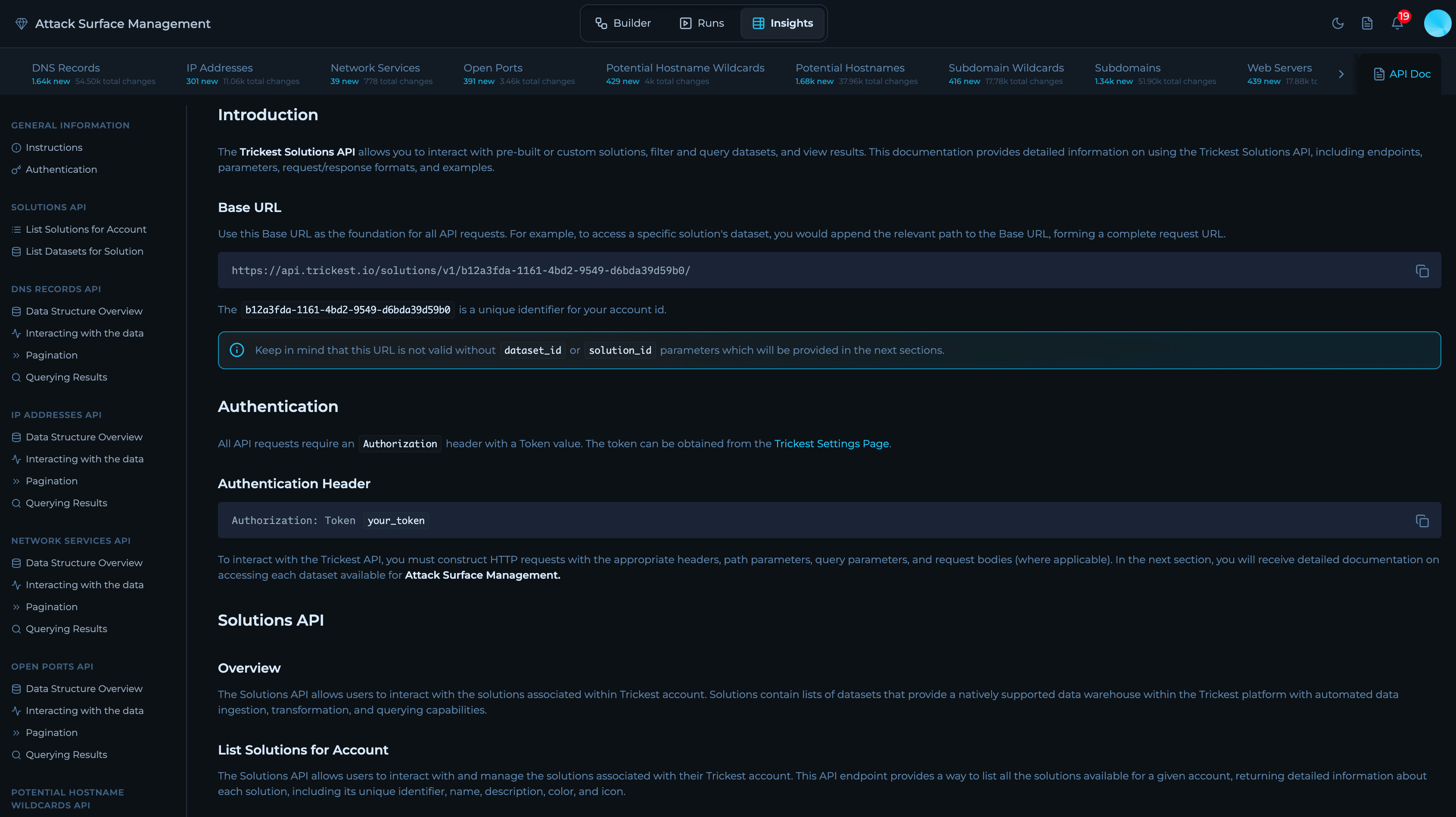
API Docs button. It shows the correct base URL, your vault-scoped endpoints, and example requests you can copy and run.